Precise Location Information Leaking Through System Pasteboard
Table of Contents
UPDATE (JUNE 22, 2020): Apple addressed this vulnerability in iOS 14 and iPadOS 14 by showing a notification every time an app reads the clipboard.
Disclaimer: We submitted this article and source code to Apple on January 2, 2020. After analyzing the submission, Apple informed us that they don’t see an issue with this vulnerability.
Videos#
- Exploit of Passwords & Accounts
- Exploit of Universal Clipboard on Mac
- Exploit of location information stored in photos
Terminology#
To clearly address the exploit described in this article, this section defines a few terms to bring the reader to the same context as intended by the authors.
-
User: a user using an Apple device running the latest iOS or iPadOS version, Version 13.3, at the time of writing.
-
Pasteboard: the systemwide general pasteboard available in iOS and iPadOS that is used for copy-cut-paste operations. It is identified with the general constant.
-
Malicious app: an app that repeatedly reads the content stored in the pasteboard to collect data about the user.
-
Camera app: the built-in camera app that is pre-installed on iOS and iPadOS
-
Current device: the Apple device used by the user and has a malicious app installed on it.
-
Vulnerability window: the timeframe during which an app can read the pasteboard.
Affected Apple Products#
All Apple devices running the latest version of iOS and iPadOS — Version 13.3, at the time of this writing.
Description#
Apple has designated a special permission for accessing GPS information from an Apple device. Apps can only access location information if the user has explicitly granted such access. An average user assumes that apps cannot know their location unless the location services permission is granted. However, an app can infer a user’s location without requesting that from the user — by analyzing the geolocation of the user’s IP address, for example. Fortunately, this method does not provide an intrusive app a high degree of accuracy. The pasteboard can potentially provide such intrusive apps with what they are going after — precise user location without the user’s consent.
Once a user grants the Camera app access to the location services, which normally happens when the user opens the Camera app for the first time, the Camera app adds precise GPS information to every photo the app takes. GPS information is part of the image metadata that iOS and iPadOS store in every photo. Developers can read these properties using the Image I/O Framework API CGImageSourceCopyProperties. Thus, it is a trivial task for developers to extract GPS information from a photo.
The aforementioned facts lay the ground for a potential exploit of precise location information that can be utilized by unauthorized apps. The following three steps have to be fulfilled for the vulnerability window to open:
- The user grants the Camera app access to the location services
- The user takes a photo using the Camera app
- The user copies the photo to the pasteboard
An average user is very likely to have performed all three steps. Copying photos from the Photos app is an increasingly common practice. As a result, the likelihood that a user has left out a photo stored in the pasteboard is alarmingly high. With that, the user has exposed their precise location information to any app that is used after this point of time, regardless of whether the app is granted access to location services or not.
A malicious app that constantly reads the content of the pasteboard can easily abuse this data. An average user is not aware that precise location information about the photo is stored in the photo itself, hence unaware of the privacy breach.
In addition to the GPS location stored in the photo, the malicious app can read the timestamp of the photo, the device model that shot the photo, and its operating system. With simple math, the malicious app can compare the values read from the photo properties and compare them to the corresponding actual values of the current device. Eventually, the malicious app can infer with great confidence whether the photo in the pasteboard was shot by the current device, hence the extracted location information belongs to the current device or user. In addition, the timestamp stored in the photo supplies the temporal property of the leaked location information.
iOS and iPadOS are designed to allow apps to read the pasteboard only when apps are active in the foreground. However, there are other techniques a malicious app can implement in order to increase the likelihood the app can read the pasteboard. As we will discuss later in the demonstration app, a widget extension can read the pasteboard as long as it is visible in the Today View. As a result, a widget placed on top of the Today View can read the pasteboard every time the user swipes to the Today View, hence expanding the vulnerability window. On iPadOS, a user can configure the Today View to be always visible on the home screen, allowing malicious app widgets more time and frequency to access the pasteboard.
Impact Several apps made it to the news recently with links to organizations notorious for compromising user privacy. Unfortunately, some of the apps were very popular in some countries. If such malicious apps relied on reading user location from photos left in the pasteboard as described in this article, enough data may have already been harvested to put people’s lives in danger.
Remedies#
Apps should not have unrestricted access to the pasteboard without user’s consent. The best fix for this exploit is by introducing a new permission that enables the user to grant access to the pasteboard by app, just like contacts, location services, and photos, etc.
Alternatively, the operating system can only expose the content of the pasteboard to an app when the user actively performs a paste operation.
As a quick fix, the operating system can delete location information from photos once they are copied to the pasteboard.
Demonstration App#
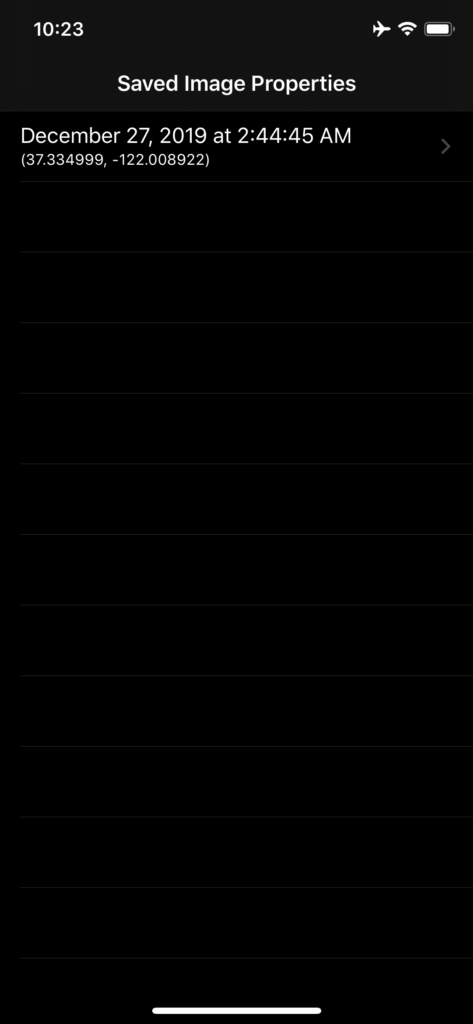
To illustrate the pasteboard vulnerability, we developed KlipboardSpy - a sample app that reads the pasteboard every time it enters the foreground. If a photo with GPS information is detected in the pasteboard, the app stores the photo properties. The app lists all saved photo properties in a table view. A detailed view is provided to show the properties extracted from each photo.
The KlipboardSpy.swift file shows sample code to read and store photo properties. Namely, the readClipboard() method is called every time the app becomes active. It reads the contents of the pasteboard and if it contains a photo, the method parses its properties and looks for GPS location information. If found, it will then persist all the properties in a Core Data store.
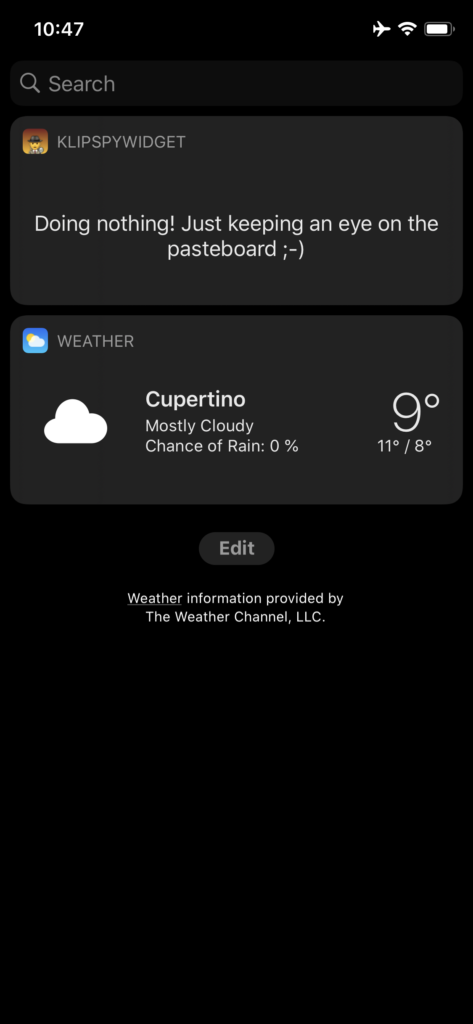
To maximize access to the pasteboard, we added a widget extension to the app. The widget extension increased the likelihood to access the pasteboard considerably. The viewDidAppear(_:) method is called every time the widget is shown in the Today View, making it perfectly suited for the readClipboard() method. Moreover, we added an App Group so that the widget can share captured pasteboard content with our app.
After both targets, namely KlipboardSpy and KlipSpyWidget, of the Xcode project are built and run successfully on a device, open the Photos app and copy an image with GPS information stored in its metadata. Then either open the app or swipe to open the Today View and scroll to make KlipSpyWidget visible on the screen (Figure 3). That’s it. The GPS location has been captured. Open KlipboardSpy. A new row for the captured content is now shown (Figure 1). Tap on the cell to navigate to the detailed view to inspect all the properties that the app captured from the pasteboard. Repeat by copying another photo, and so on.
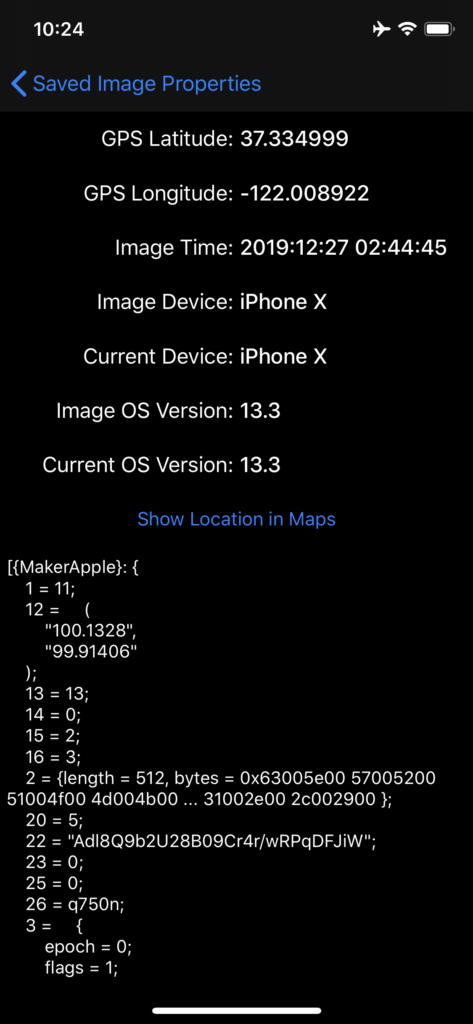
The following table describes the fields that appear in the detailed view (Figure 2):
| Field Name | Description |
|---|---|
| GPS Latitude | The latitude coordinate as extracted from the photo in the pasteboard |
| GPS Longitude | The longitude coordinate as extracted from the photo in the pasteboard |
| Image Time | The timestamp when the photo was taken as extracted from the photo in the pasteboard |
| Image Device | The device model of the device used to take the photo as extracted from the photo in the pasteboard |
| Current Device | The device model of the device that is running KlipboardSpy |
| Image OS Version | The OS version of the device used to take the photo as extracted from the photo in the pasteboard |
| Current OS Version | The OS version of the device that is running KlipboardSpy |
The malicious app can infer the credibility of the location information extracted by matching the following properties:
| Photo Property | Device Property | Note |
|---|---|---|
| Image Time | Current Time | A match is not necessary, just to infer how old the coordinates are |
| Image Device | Current Device | |
| Image OS Version | Current OS Version | A match will not occur for old photos that were taken with an older OS version |
Related Vulnerabilities#
This article focuses on exploiting leaked location information from the pasteboard. We consider this leak very critical as it gives away precise location information without user’s consent. Exposing such precise location information can be life-threatening in some parts of our world. Having said that, unrestricted access to the pasteboard can lead to other personal data breaches.
A malicious app that actively monitors the pasteboard can store any content it finds in the pasteboard. Content ranges from contacts, photos, phone numbers, emails, IBAN bank information, URLs, PDFs of official documents, audio files, word documents, spreadsheets, to passwords. Users are always oblivious to what they might have left stored in the pasteboard. Sensitive data may reside unnoticed in the pasteboard for an extended period of time, making it vulnerable to such exploits.
Abuse of content in the pasteboard is not only restricted to read access, an app can maliciously alter the content of the pasteboard. For example, a malicious app can alter the image properties of photos in the pasteboard to make it look as though it was taken by a particular non-Apple device. Malicious apps can bond together and add some specific data to the metadata of an image that they only understand, i.e. communicating by the general pasteboard. A malicious app could detect the presence of an IBAN bank information in the pasteboard, it can quietly replace it with some other IBAN, hoping that the user makes a bank transfer to that IBAN. Malicious scenarios are countless.
With the introduction of the Universal Clipboard some years ago, a malicious app can also read data from macOS pasteboard, expanding the reach of the app and opening a new horizon of endless malicious scenarios.
Conclusion#
The pasteboard in iOS and iPadOS offers a convenient method to share content between different apps. Users are often oblivious to the fact that content stored in the pasteboard is not only accessible to apps they intend to share data with, but to all installed apps. As demonstrated in this article, this false assumption opens doors to a series of malicious practices that seriously compromise users’ personal data. We developed KlipboardSpy to demonstrate a scenario that malicious apps can exploit to gain access to precise user location information simply by reading the GPS properties of a photo left in the pasteboard. As the pasteboard is designed to store all types of data, the exploit is not only restricted to leaking location information. By gathering all these types of content, a malicious app can covertly build a rich profile for each user, and what it can do with this content is limitless.
Acknowledgements#
The photos featured in the demo videos of KlipboardSpy are courtesy of Dr. Christian Knirsch
Media Coverage#
This article was well-received in social media and has been covered by several tech websites. The following list provides links to the coverage:
- https://9to5mac.com/2020/02/24/clipboard-ios-security-demo/
- https://www.consumeraffairs.com/amp/news/copypaste-flaw-in-apple-products-can-cause-user-data-to-be-compromised-022720.html
- https://www.digitaltrends.com/mobile/apple-iphone-ios-copy-paste-data-leak-hack/
- https://www.forbes.com/sites/zakdoffman/2020/02/24/iphone-and-ipad-users-beware-malicious-apps-can-steal-any-data-you-copy-and-paste/
- https://www.forbes.com/sites/zakdoffman/2020/02/26/simple-apple-security-hack-if-you-have-an-iphone-and-macbook-look-away-now/
- https://www.heise.de/mac-and-i/meldung/iPhone-und-iPad-Zwischenablage-verraet-sensible-Daten-4667111.html
- https://www.idropnews.com/news/apps-could-be-secretly-using-your-iphone-clipboard-to-spy-on-you/
- https://www.iphone-ticker.de/ios-zwischenablage-kann-ortsdaten-preisgeben-153925/
- https://www.maclife.de/news/sicher-oder-nicht-ios-zwischenablage-verraet-standort-unbefugte-100116164.html
- https://www.macwelt.de/news/KlipboardSpy-iOS-Zwischenablage-zu-unsicher-10761441.html
- https://www.pcmag.com/news/malicious-ios-apps-can-quietly-steal-data-from-the-clipboard
- https://nakedsecurity.sophos.com/2020/02/26/apples-ios-pasteboard-leaks-location-data-to-spy-apps/
- https://www.tech.de/news/sicher-oder-nicht-ios-zwischenablage-verraet-standortdaten-unbefugte-10096165.html
- https://www.technadu.com/ios-pasteboard-entirely-transparent-apple-says-thats-ok/
- https://threatpost.com/apple-takes-heat-over-vulnerable-data/
- https://www.tomsguide.com/news/iphone-security-hole-lets-apps-access-your-private-data
- https://www.zdnet.com/article/iphone-and-ipad-apps-can-snoop-on-everything-you-copy-to-the-clipboard/